Guides
Self-Service Cloud
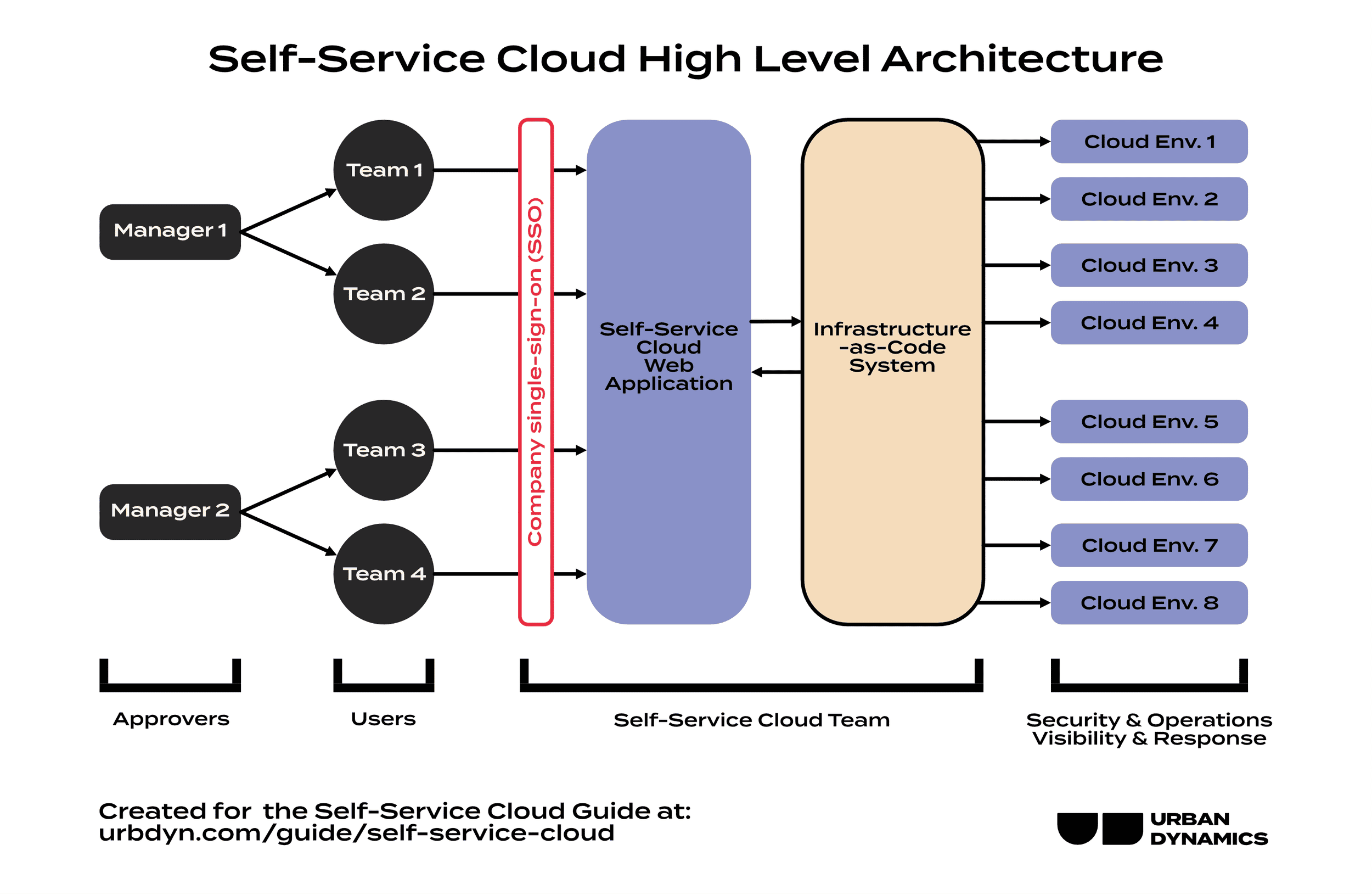
Self-Service clouds are a solution that empowers all parts of a business to move quickly to changing needs while ensuring the proper top-level guard rails and visibility exist. We at Urban Dynamics are strong believers that a tool is only as good as it is useful, and making a cloud self-service is how to make it the most useful to the most people. It benefits a business by adding efficiency, agility, security, and standardization to their cloud environments.
Continue Reading →